Data Objects
Introduction
Imagine that you would like to associate specific information with a license key, such as your customer's name, the OS version, etc.
Data Objects enable your application to store variables in the cloud in a way that empowers your licensing process. Think of them as additional variables that can be added to a license key, a product or the entire account.
What is a Data Object?
Data Object can be thought of as way to store integers and strings that can later be retrieved anywhere, anytime. For those that understand UML, here is a visual representation of a data object.
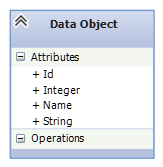
A data object contains the following fields:
- Id - It's a unique identifier of the data object.
- Name - It's like a variable name. Note, several objects can have the same name. A name can be 10 chars at most.
- String Value - This is the content of the data object. It can store a string of 10000 chars.
- Int Value - The integer value of the data object. It can store a 32 bit signed integer.
- User - Your entire account. The ReferencerId does not need to be specified.
- Product - A specific product. The ReferencerId is the productId, aka pid.
- Key - A specific license key. The ReferencerId is the keyId, aka sid.
Related Methods
- Add Data Object - Creates a new data object.
- List Data Objects - List existing data objects.
- Increment Int Value - Increments the IntValue by certain constant.
- Decrement Int Value - Decrements the IntValue by a certain constant.
- Set String Value - Set a new StringValue.
- Set Int Value - Set a new IntValue.
- Remove Data Object - Remove an existing Data Object.
Permissions using Access Tokens
As with other methods in the Web API, you can easily customize the permission/scope of each method. To enable access to a method, you need to create an Access Token that enables access to the method. In addition, Data Objects have further permission settings. They are summarized below:
- To create a data object associated with a User, both the product lock and the key lock should be disabled (set to zero).
- To create a data object associated with a Product, no key lock should be present (i.e. set to zero) and the product lock should either be disabled or set to the desired product id.
- To create a data object associated with a Key, there should not be any product lock on a product that this key does not originate from, and there should not be any key lock on a key other than this one.
- For methods Increment Int Value and Decrement Int Value, you can use the Feature lock field in the Access Token as a way to specify the upper bound.
- (Not needed anymore. Just use specialized methods.)To work with data objects from the client application (low trust), the Key Lock method should be used instead. The idea is that you create a generic Access Token, which can be converted into a scope-limited Access Token given a license key string. Moreover, it comes with the advantage that you get the KeyId, which can then be used as a ReferencerId. You can read more here.
 Made in Sweden
Made in Sweden